Encrypted Standard Strings & PowerShell
Notes about encryption/decryption in Windows PowerShell scripts (..ps1), Secure Strings vs. Encrypted Standard Strings, and some PowerShell code tips.
The
ConvertTo-SecureStringandConvertFrom-SecureStringcmdlets based their encryption key on the identity of the user logged in. … It allows me to encrypt a string and save it to a file but prevents anyone else from reading the same file and decrypting the same string. A system wouldn’t be very secure if anyone could come along and decrypt files that others had encrypted.
Secure Strings vs. Encrypted Standard String: https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.security/convertfrom-securestring?view=powershell-7.3
https://www.red-gate.com/simple-talk/sysadmin/powershell/powershell-and-secure-strings/
https://www.red-gate.com/simple-talk/sysadmin/powershell/powershell-and-secure-strings/
Makes a file name with the User Name in it.
$LocalFilePath='C:\temp'
if (-not (test-path $LocalFilePath\cred_$env:UserName.txt))
{
read-host -AsSecureString | ConvertFrom-SecureString | Out-File $LocalFilePath\cred_$env:UserName.txt
"Setting Password first time for $env:UserName" | out-file $LocalFilePath\app_log.txt -append
} https://medium.com/@nikhilsda/encryption-and-decryption-in-powershell-e7a678c5cd7d
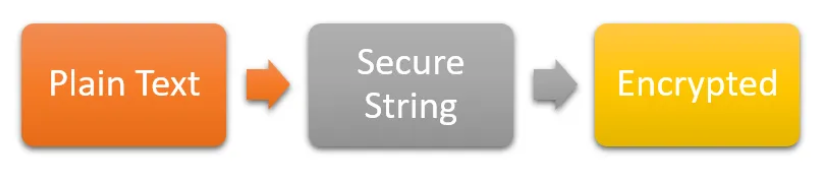
The point of converting your password to a SecureString and storing it in a file is to 1) keep it out of plain text in your scripts so that it’s not as easily discovered and 2) only allow the user who created the password file to decrypt the password in it. This will not stop anybody who can logon to Windows with your credentials and knows PowerShell from decrypting your password. It’s not foolproof, but it’s pretty good.
Export SecureString from Get-Credential
(Get-Credential).Password | ConvertFrom-SecureString | Out-File "C:\Temp 2\Password.txt"
Decryption
[System.Net.NetworkCredential]::new("", $securePassword).Password
